Secure Software Development: Why it Matters
In today’s digital age, software development has become an integral part of our lives. From mobile apps to web applications, software is used to power everything we do online. However, with the rise of cyber threats and attacks, securing software has become more important than ever before.
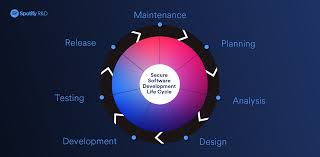
Secure software development is the process of designing, building, testing and deploying software that is resistant to attacks and vulnerabilities. It involves implementing security measures throughout the entire software development lifecycle (SDLC), from planning and design to deployment and maintenance.
The importance of secure software development cannot be overstated. Cybercriminals are constantly looking for vulnerabilities in software to exploit for their own gain. A single vulnerability can lead to data breaches, financial loss, reputational damage, and even legal consequences.
By implementing secure software development practices, developers can reduce the risk of vulnerabilities in their code. This includes using secure coding practices such as input validation, error handling, authentication and authorization mechanisms, encryption techniques and more.
One key aspect of secure software development is testing. Developers must thoroughly test their code for vulnerabilities before releasing it into production. This includes using automated tools such as static analysis tools that scan code for potential security flaws.
Another important aspect of secure software development is keeping up-to-date with the latest security trends and threats. Developers must be aware of new attack vectors and vulnerabilities that could affect their code. They must also keep up-to-date with patches and updates released by vendors to address known vulnerabilities.
Secure software development is not just important for businesses but also for individual users who rely on software applications every day. Users expect applications to be secure by default so that they can trust them with their sensitive information.
In conclusion, secure software development should be a top priority for all developers regardless of the size or complexity of their projects. By implementing secure coding practices, thorough testing procedures and staying up-to-date with the latest security trends and threats, developers can ensure that their software is secure and resistant to attacks. This will not only protect businesses from cyber threats but also build trust among users who rely on software applications for their daily tasks.
7 Essential Tips for Secure Software Development
- Plan Security from the Beginning
- Use Secure Coding Practices
- Test Early and Often
- Perform Security Reviews
- Utilize Automated Tools
- Encrypt Sensitive Data
- Monitor Your Software Regularly
Plan Security from the Beginning
When it comes to software development, security should not be an afterthought. It should be planned from the beginning. This means that security considerations should be integrated into every stage of the software development lifecycle (SDLC), from planning and design to deployment and maintenance.
Planning for security from the beginning is important because it helps developers identify potential security risks early on in the development process. This allows them to address these risks before they become bigger problems down the line.
One way to plan for security from the beginning is to conduct a threat analysis during the planning phase of the SDLC. This involves identifying potential threats and vulnerabilities that could affect the software application, as well as assessing their impact and likelihood.
Another important aspect of planning for security from the beginning is to establish secure coding practices. Developers should follow established coding standards and guidelines that include secure coding practices such as input validation, error handling, authentication and authorization mechanisms, encryption techniques, and more.
In addition, developers should also consider implementing security testing procedures throughout the SDLC. This includes using automated tools such as static analysis tools that scan code for potential security flaws.
By planning for security from the beginning, developers can ensure that their software applications are secure by design. This helps prevent vulnerabilities from being introduced into their code later on in the development process or after deployment.
In conclusion, planning for security from the beginning is an essential aspect of secure software development. It helps identify potential risks early on in the SDLC and allows developers to address them before they become bigger problems down the line. By integrating security considerations into every stage of the SDLC, developers can ensure that their software applications are secure by design and resistant to attacks.
Use Secure Coding Practices
When it comes to secure software development, one of the most important tips is to use secure coding practices. Secure coding practices are a set of guidelines and techniques that developers can use to write code that is resistant to attacks and vulnerabilities.
Secure coding practices include input validation, error handling, authentication and authorization mechanisms, encryption techniques and more. These practices ensure that the code is free from vulnerabilities that could be exploited by cybercriminals.
Input validation is an essential part of secure coding practices. It involves checking user input for malicious or unexpected data. This prevents attackers from injecting malicious code into the application through user input.
Error handling is another important aspect of secure coding practices. It involves handling errors in a way that does not reveal sensitive information about the application or the system it is running on. Proper error handling also ensures that the application does not crash or become unstable in case of errors.
Authentication and authorization mechanisms are essential for securing applications that require user authentication. These mechanisms ensure that only authorized users can access certain parts of the application or perform certain actions.
Encryption techniques are also important for securing data in transit and at rest. Encryption ensures that data cannot be read by unauthorized parties even if it is intercepted during transmission or stolen from storage.
In conclusion, using secure coding practices is crucial for developing software applications that are resistant to attacks and vulnerabilities. By implementing these practices, developers can ensure that their code is free from vulnerabilities and can protect users’ sensitive information from cyber threats.
Test Early and Often
Test Early and Often: A Key Tip for Secure Software Development
In the world of software development, testing is a critical component of ensuring that software is secure and free from vulnerabilities. The earlier you test your software, the easier it is to address any issues that may arise.
This is why testing early and often is a key tip for secure software development. By testing early in the development process, developers can catch potential vulnerabilities before they become more difficult and expensive to fix later on.
Testing early also allows developers to identify any design flaws or other issues that could lead to security vulnerabilities down the line. This can help prevent costly rework and delays in the development process.
In addition, testing often throughout the development process helps ensure that any changes made do not introduce new vulnerabilities. As code is added or modified, it’s essential to test frequently to ensure that no new security issues have been introduced.
Automated testing tools can be particularly useful in this regard. These tools can scan code for potential security flaws and provide developers with feedback on how to fix them.
Overall, testing early and often should be a top priority for all developers looking to create secure software. By catching potential vulnerabilities early on and ensuring that changes do not introduce new issues, developers can create software that is resistant to attacks and protects both businesses and users alike.
Perform Security Reviews
Perform Security Reviews: A Crucial Step in Secure Software Development
When it comes to secure software development, one of the most important steps is performing security reviews. Security reviews involve analyzing code, architecture, and design for potential vulnerabilities and threats.
Performing security reviews should be an integral part of the software development lifecycle (SDLC). It should be done during the planning and design phase and then continuously throughout the development process. This helps to identify potential security issues early on in the process, making them easier and less expensive to fix.
There are several types of security reviews that can be performed during the SDLC. These include code reviews, architecture reviews, and design reviews. Code reviews involve analyzing source code line by line to identify vulnerabilities such as buffer overflows or SQL injection attacks. Architecture reviews focus on identifying potential security weaknesses in the overall system architecture. Design reviews focus on identifying potential security weaknesses in system design.
Performing regular security reviews is important because it helps to ensure that software is secure by default. It also helps to identify any vulnerabilities or threats that may have been missed during previous phases of development.
In conclusion, performing regular security reviews is a crucial step in secure software development. It helps to identify potential vulnerabilities and threats early on in the process, making them easier and less expensive to fix. By implementing this practice as part of your SDLC, you can ensure that your software is secure by default and protect against cyber threats that could harm your business or users’ sensitive information.
Utilize Automated Tools
Utilizing Automated Tools for Secure Software Development
Secure software development is critical to protect against cyber threats and vulnerabilities. One important aspect of secure software development is utilizing automated tools to scan code for potential security flaws.
Automated tools can help developers identify potential vulnerabilities in their code early in the development process. This enables them to fix issues before the code is released into production, reducing the risk of costly security breaches down the line.
There are a variety of automated tools available for secure software development, including static analysis tools, dynamic analysis tools, and penetration testing tools. These tools can analyze code for common security issues such as buffer overflows, SQL injection, and cross-site scripting (XSS) attacks.
Static analysis tools scan source code without executing it, identifying potential vulnerabilities before the application is compiled or executed. Dynamic analysis tools analyze running applications to identify potential vulnerabilities in real time. Penetration testing tools simulate attacks on an application to identify potential vulnerabilities that could be exploited by attackers.
By utilizing automated tools throughout the software development lifecycle, developers can ensure that their code is secure and resistant to attacks. These tools can also save time and resources by identifying potential vulnerabilities early in the development process, reducing the need for costly manual testing later on.
In conclusion, utilizing automated tools for secure software development is a crucial step in protecting against cyber threats and vulnerabilities. Developers should incorporate these tools into their development processes to ensure that their code is secure and resistant to attacks from malicious actors.
Encrypt Sensitive Data
Encrypt Sensitive Data: A Key Tip for Secure Software Development
One of the most important tips for secure software development is to encrypt sensitive data. Encryption is the process of converting plain text into a coded format that can only be read by authorized parties. By encrypting sensitive data, developers can ensure that it remains secure even if it falls into the wrong hands.
Sensitive data includes personally identifiable information (PII), financial information, and other confidential information that could cause harm if it were to be accessed by unauthorized parties. This type of data is often stored in databases or transmitted over networks, making it vulnerable to cyber attacks.
Encrypting sensitive data involves using cryptographic algorithms to scramble the data in a way that makes it unreadable without the proper encryption key. This ensures that even if an attacker gains access to the data, they will not be able to read or use it.
There are many different encryption algorithms available, each with its own strengths and weaknesses. Developers must choose an algorithm that is appropriate for their specific use case and ensure that it is implemented correctly.
In addition to encrypting sensitive data at rest (stored in databases), developers must also ensure that data is encrypted in transit (transmitted over networks). This involves using secure communication protocols such as HTTPS, SSL/TLS, or SSH.
Encrypting sensitive data is not a one-time process but rather an ongoing effort. Developers must regularly review their encryption practices and update them as needed to ensure that they remain effective against new threats and vulnerabilities.
In conclusion, encrypting sensitive data is a crucial tip for secure software development. By implementing strong encryption algorithms and ensuring that data is encrypted both at rest and in transit, developers can protect sensitive information from cyber attacks and maintain user trust.
Monitor Your Software Regularly
Secure Software Development: Monitor Your Software Regularly
Monitoring your software regularly is an essential aspect of secure software development. It involves keeping an eye on your software applications to ensure that they are functioning as intended and are not vulnerable to attacks.
Regular monitoring helps identify security vulnerabilities that may arise due to changes in the environment or codebase. It enables developers to detect and fix potential security flaws before they can be exploited by cybercriminals.
Monitoring should be done throughout the entire software development lifecycle, from testing and deployment to maintenance and updates. This includes monitoring for changes in user behavior, system logs, network traffic, and application performance.
One important aspect of monitoring is keeping an eye on third-party components used in the application. These components may have vulnerabilities that could be exploited by attackers. Regularly checking for updates and patches released by vendors can help ensure that these components are secure.
Another important aspect of monitoring is identifying unusual activity or behavior within the application. This could include unauthorized access attempts, excessive login attempts, or unusual data transfer patterns. Identifying such activity early can help prevent data breaches or other malicious activities.
In conclusion, regular monitoring is a critical aspect of secure software development. It helps identify potential security flaws early on so that they can be addressed before they can be exploited by attackers. By keeping an eye on your software applications throughout their lifecycle, you can ensure that they remain secure and function as intended.